What Is Error 403 Forbidden from Cloudflare
Error 403 from Cloudflare is a forbidden status code. You get this response when trying to scrape a website as a bot. That can happen when using tools like Python, NodeJS, cURL, etc. The security service assumes you're a threat and displays an Error 1020 screen, representing the 403 status code.
Let's see how to avoid that.
How to Bypass Cloudflare 403 Forbidden Error
Here are four solutions to bypass the 403 web scraping error from Cloudflare.
1. Use a Web Scraping API
Web scraping APIs like ZenRows are designed to handle the complexities of a Cloudflare 403 Forbidden bypass. It's an all-in-one tool that gets around all anti-bot challenges and is easy to use.
Let's try ZenRows to scrape Notion's reviews page on G2, which is a sample Cloudflare-protected URL. All you need to get started is sign up to get your free API key, and you'll get to the Request Builder page:
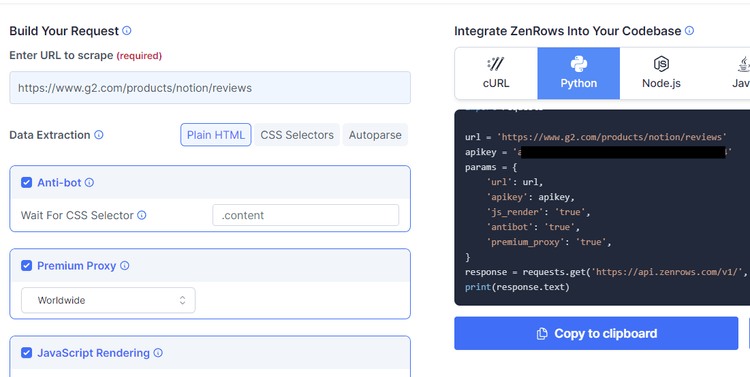
Now, select "Python" (although ZenRows works with any language) and pass in the target URL. Next, check the boxes for "Anti-bot", "Premium Proxy", and "JavaScript Rendering" to set their parameters to true:
Then, copy the code into your favorite editor and install Install the Python Requests library using the following command:
Here's the complete code:
# pip install requests
import requests
url = 'https://www.g2.com/products/notion/reviews'
apikey = '<YOUR_ZENROWS_API_KEY>'
params = {
'url': url,
'apikey': apikey,
'js_render': 'true',
'antibot': 'true',
'premium_proxy': 'true',
}
response = requests.get('https://api.zenrows.com/v1/', params=params)
print(response.text)
Your result should look like this:
#..
<title>Notion Reviews 2024: Details, Pricing, & Features | G2</title>
#..
<h1 class="l2 pb-half inline-block">Notion Reviews & Product Details</h1>
You can test this tool directly on the Request Builder page by clicking the "Try It" button.
Congrats, you've bypassed Cloudflare with Python and Zenrows!
2. Get Premium Proxies
Web scraping proxies act as middlemen between you and a target server, allowing you to route your requests through different IP addresses. While free proxies are readily available, they often present challenges, such as slower speeds, high fail rates, and a high chance of being detected.
Premium proxies, on the other hand, are more reliable, with stable connections and higher chances of avoiding detection. Furthermore, residential proxies offer IP addresses assigned to real devices. That way, you appear as a natural user and, ultimately, bypass the Cloudflare 403 Forbidden Error.
3. Bypass Fingerprinting with a Headless Browser
Cloudflare leverages various security techniques, including TLS fingerprinting, to identify and block web clients accordingly. During a TLS handshake, Cloudflare analyzes multiple parameters to determine if the incoming request is legitimate or potentially malicious.
Requests from non-browser sources like HTTP libraries are tagged malicious, hence the Cloudflare 403 Forbidden Error. However, by simulating human-like behavior, you can avoid this issue.
Headless browsers like Puppeteer, Selenium, and Playwright enable you to simulate a full browser environment, including JavaScript rendering, DOM manipulation, cookie handling, etc. Check out our guide on how to bypass TLS fingerprinting to learn more.
4. Fortify Your Headless Browser
While headless browsers can help you imitate human behavior, you may still get blocked. That is often associated with automation properties, such as navigator.webdriver=true, which identify you as a bot. So, you'll need to fortify your web scraper to bypass Cloudflare 403 Forbidden Error.
Tools like Undetected ChromeDriver for Selenium hide the base tools' automation properties and make your headless browser appear as a regular one.
Did you find the content helpful? Spread the word and share it on Twitter, or LinkedIn.