CAPTCHAs can hinder any web scraping project and are becoming increasingly challenging. Fortunately, there are ways to bypass CAPTCHA while web scraping, and we'll cover seven proven techniques:
- Rotate IPs.
- Rotate User-Agent strings.
- Use a CAPTCHA resolver.
- Avoid hidden traps.
- Simulate human behavior.
- Save cookies.
- Hide automation indicators.
What Is CAPTCHA
CAPTCHA is a short way to say "Completely Automated Public Turing test to tell Computers and Humans Apart". It's a security measure to prevent automated programs from accessing websites, protecting them from potential harm.
That test is easy for humans to solve but difficult for machines to understand. For example, in the image below, the user must check the box to prove they're human.
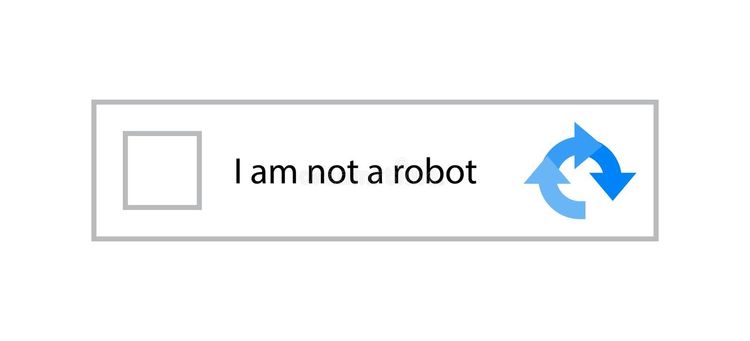
Can CAPTCHA Be Bypassed
In general, CAPTCHAs can be bypassed, but it's challenging. The most recommended approach is to prevent them from appearing in the first place and, if blocked, to retry the request. Alternatively, you can solve it, but the success rate is much lower and the cost significantly higher.
Below, we'll cover both approaches for Python or any other language, giving you a better understanding of how to bypass CAPTCHAs and get the data you want.
Different CAPTCHA Types to Bypass While Scraping
It's important to understand the different CAPTCHA types you may encounter when scraping, so here are the most common ones:
- Text-based CAPTCHAs: These are the most frequent ones, which task the users to identify and enter a distorted series of text and numbers in an input field.
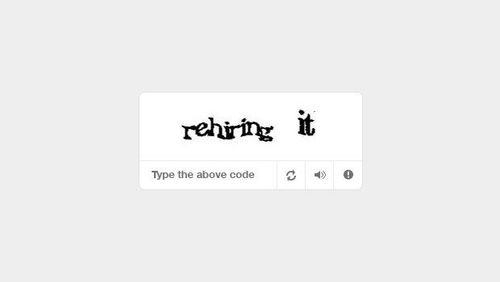
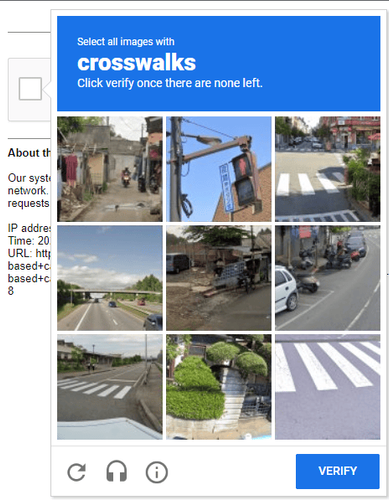
- Image-based CAPTCHAs: The user has to identify and click on specific objects in an image, like traffic lights or vehicles.
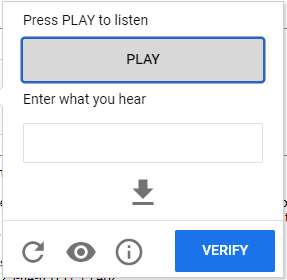
- Audio-based CAPTCHAs: Here, users have to enter what they hear from an audio clip into a text area. It's usually a series of numbers or letters.
- reCAPTCHA v2: reCAPTCHA v2 is Google's CAPTCHA system that requires users to click a checkbox to verify they're human.
- reCAPTCHA v3: This is the newest version of Google's CAPTCHA system that works in the background, and users are usually unaware of it. It uses a score to determine if the interactions on the site are human or bot-like.
How to Bypass CAPTCHA While Scraping in Python
In this section, we'll look at some techniques to bypass the frustrating CAPTCHA obstacles while scraping in Python.
1. Rotate IPs
If many requests come from the same IP address, websites detect it as bot activity and block it. To prevent that, rotate your IPs to scrape without interruptions.
You can try with free proxies, but they'll fail most times. Your best option is to use a premium CAPTCHA proxy server that masks your IP and changes the assigned address often.
If you're interested in learning more, check out our guide on rotating proxies in Python.
2. Rotate User-Agents
Rotating User-Agents is another way to prevent CAPTCHAs from appearing while scraping. This string is sent with every request and identifies the browser and operating system. The information helps websites optimize their pages for different devices and browsers, but it can also be used to identify and block bots.
You need to use User-Agents that look real, with consistent information, are up-to-date, and rotate them to avoid suspicion. Check out our list of best User Agents for web scraping to get started.
3. Use a CAPTCHA Resolver
CAPTCHA resolvers are services that automatically solve CAPTCHAs, allowing you to scrape websites without interruptions. A popular example is 2Captcha, which employs human workers to solve challenges fast and accurately.
While that appears to be an easy fix, it has important disadvantages: it'll be expensive and will work with some CAPTCHA types only.
4. Avoid Hidden Traps
Did you know that websites use sneaky traps to detect bots? For example, the honeypot trap tricks them into interacting with hidden form fields or links. That allows websites to spot bot behavior and flag the IP.
But you can learn how these traps work and how to spot them. One way is to inspect the website's HTML for hidden elements or such with unusual names or values.
You can learn more about honeypot traps and how to bypass them.
5. Simulate Human Behavior
Accurately simulating human behavior is essential to bypass CAPTCHA while scraping a website, and a headless browser will help you with tasks such as scrolling and cursor moving.
Tools like Selenium enable you to control e.g. Chrome programmatically and create headless browser sessions. Check out our in-depth guide on headless browsers in Python and Selenium to learn to implement it.
6. Save Cookies
Cookies can be your secret weapon when it comes to web scraping. These small files contain data about your interactions with a website, including your login status, preferences, etc. If you're scraping behind a login, cookies can be beneficial since they save you the hassle of logging in again and reduce the risk of getting caught.
With headless browsers like Selenium, you can programmatically save and load cookies and extract data under the radar.
7. Hide Automation Indicators
When using a headless browser, you still need to be careful because websites can identify bots by looking for automation indicators such as browser fingerprints. However, plugins such as Selenium Stealth hide those, and you can also use them to mimic human-like mouse movements and keyboard strokes.
Check out our tutorial on how to avoid bot detection with Selenium to keep your scraping activities running.
Conclusion
Preventing CAPTCHAs from hindering web scraping is no easy feat, but now, you're better equipped to tackle this challenge. However, implementing the methods mentioned above can be time-consuming and ineffective when it comes to large-scale projects.
That's where ZenRows comes in. Combining the strategies outlined in this article with others, ZenRows provides an easy and scalable solution to bypass CAPTCHAs with a single API call.
So why waste time? With Zenrows, you can freely web scrape without getting blocked.Try ZenRows out for free and discover how it can take your scraping to the next level.
Frequent Questions
How Do I Bypass CAPTCHA While Web Scraping Using Python?
If you're web scraping using Python and need to bypass CAPTCHAs, there are several techniques to increase your chances of success. For example, you can rotate IPs using a proxy service. Alternatively, you can rotate user agents, save cookies, and avoid hidden traps.
How to Bypass reCAPTCHA in Python?
If you want to bypass reCAPTCHA in Python, you can use various methods. Some are rotating user agents and IPs or use CAPTCHA resolvers to avoid detection. You can also make the most of tools like Selenium or Puppeteer to bypass CAPTCHAs.
How Do I Bypass hCAPTCHA When Scraping?
If you want to bypass hCAPTCHA when scraping, you have several options. One way is to rotate IP addresses often so the website can't detect and block your activity. Another option is to rotate User Agents to make your request look like it's coming from different devices. You can also use CAPTCHA resolvers, which solve them automatically.
Did you find the content helpful? Spread the word and share it on Twitter, or LinkedIn.